Goal : Retrieve secret values from Azure Key Vault protected by certificat with Magic xpi using REST API
1/ Generate your certificat (pfx format) and declare it in the azure console (Azure Key Vault)
You can use standard powershell script to generate and export the pfx certificate.
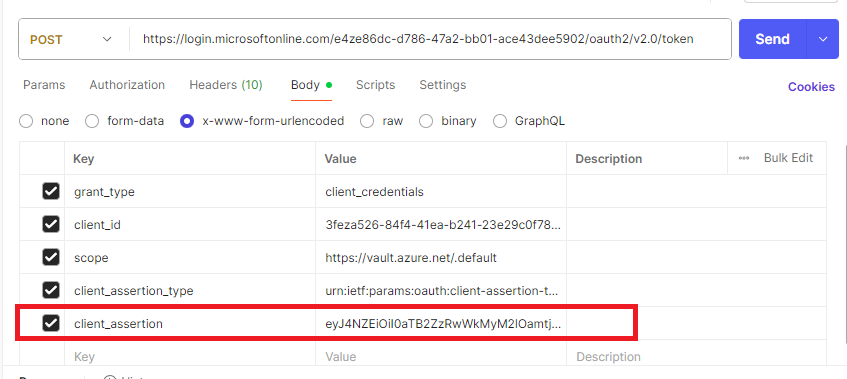
2/ To test with postman, you need first to generate the Client_Assertion in other to get the token
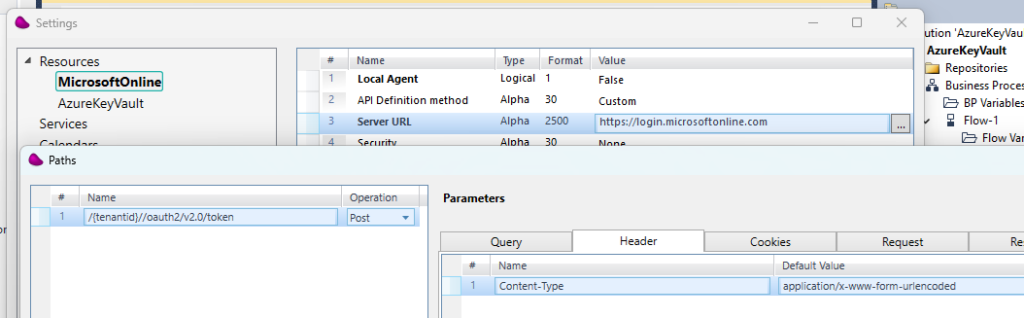
2/ Define 2 resources one for the token and one for Key Vault.
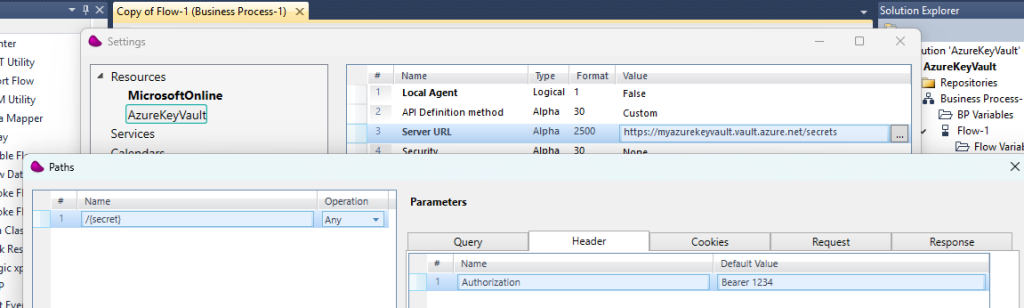
Replace <myazurekeyvault) with your own keyvault.
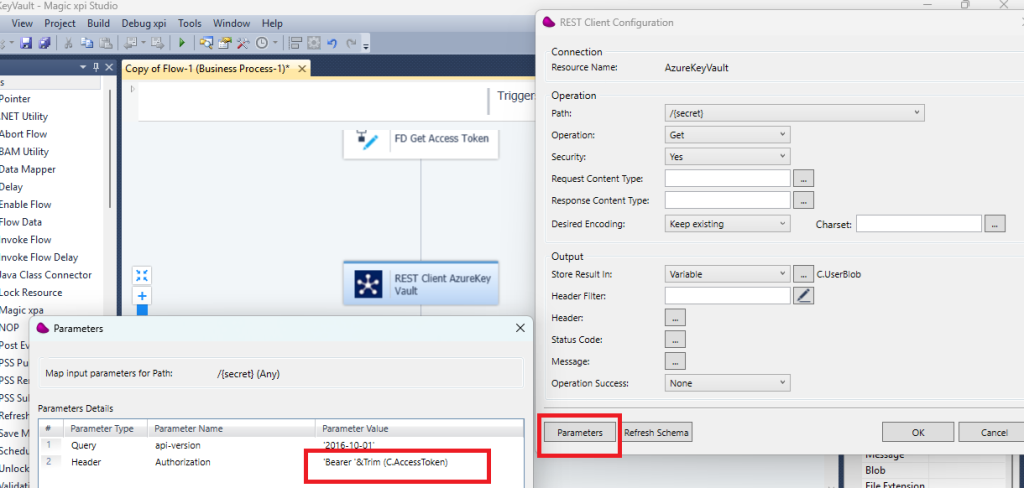
Don’t forget to set in the Query tab control : api-version with 2016-10-01
3/ To Generate the Client_Assertion, we will use a piece of java code
We are going to use a Java Class AzureKeyVault with method getClientAssertion. We will call this method with Magic JcallStatic function.
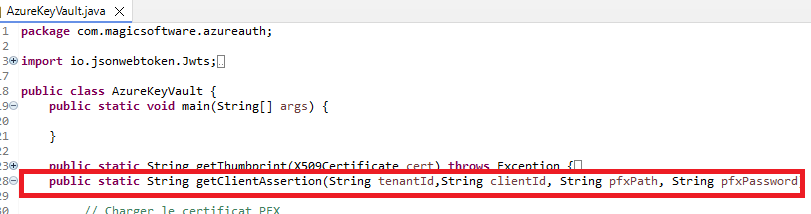
This signature function will accept 4 parameters (tenantId, clientId, pfxPath and pfxPassword).
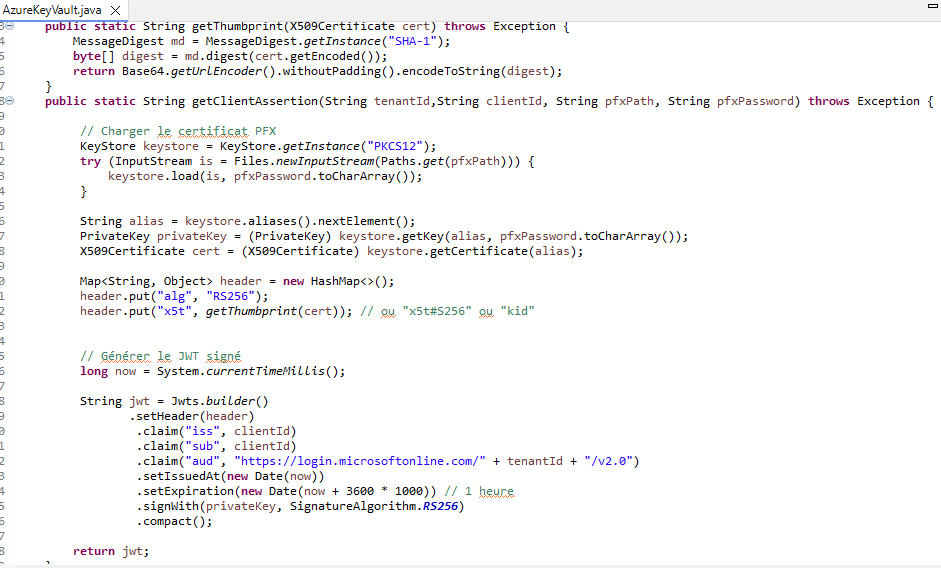
Drag and drop a Flow data connector in your Magic xpi flow
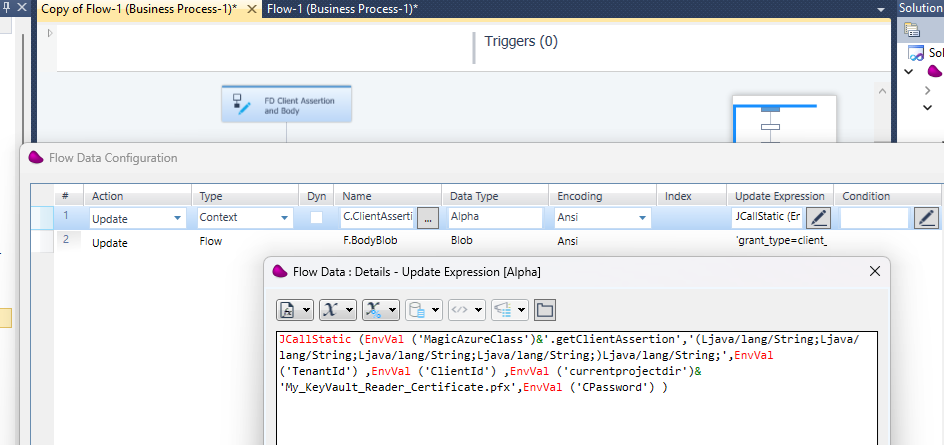
Define 2 variables C.ClientAssertion (alpha unlimited) and F.BodyBlob (Blob).
Update your context variable with JCallStatic function (see Magic xpa Help for the syntax)
MagicAzureClass environment Variable has the value : com.magicsoftware.azureauth.AzureKeyVault
TenantID corresponds to your azure tenant Id as well as for ClientId to azure client id and CPassword for certificate password
The second operation updates the body request that will be used for the getting the token.
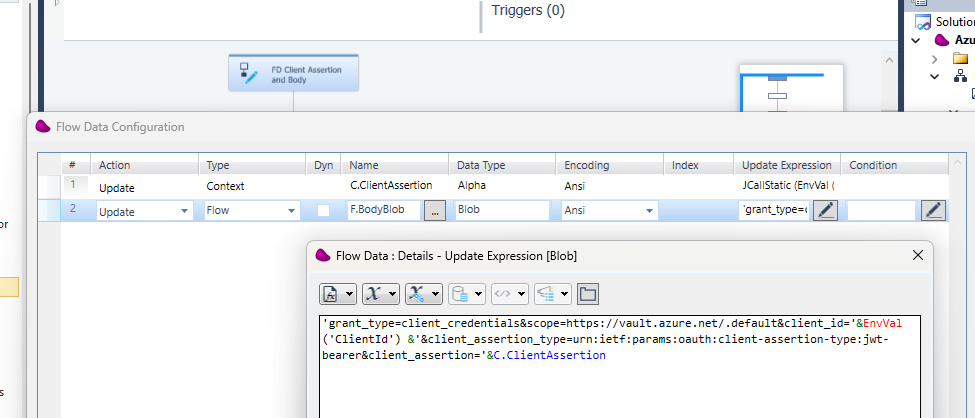
!! You must copied 4 jar files inside your Magic xpi runtime\java\lib folder
4/ Drag and drop REST Client connector and link it to the MicrosoftOnline resource
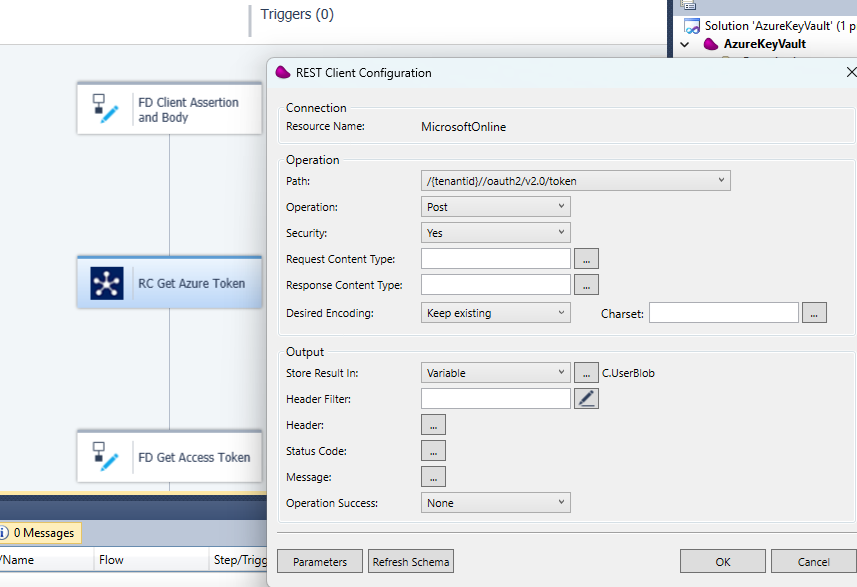
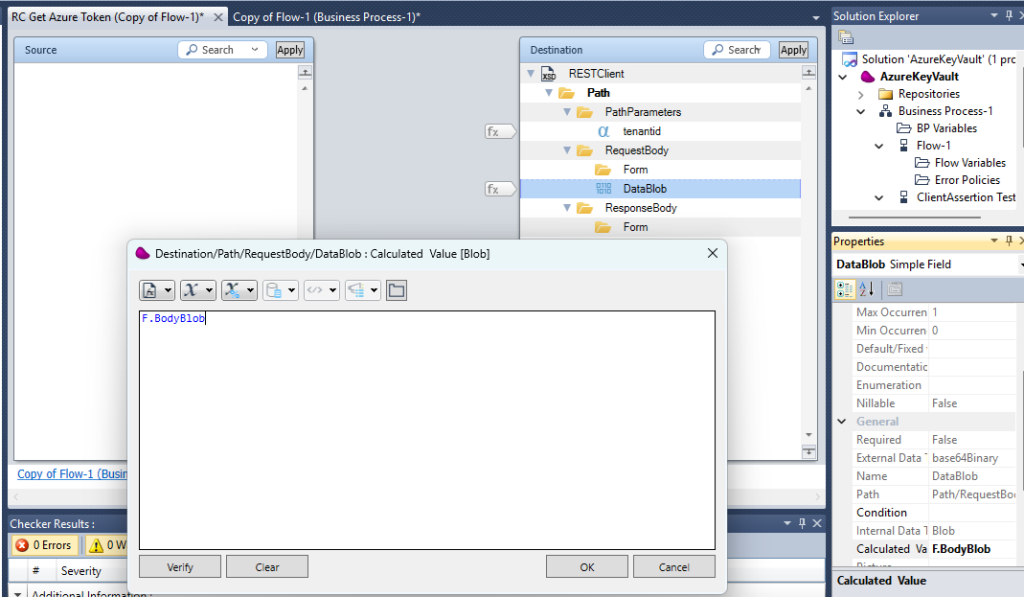
Press OK and set the tenantid with your tenant and DataBlob your Flow variable F.BodyBlob (updated in the previous step)
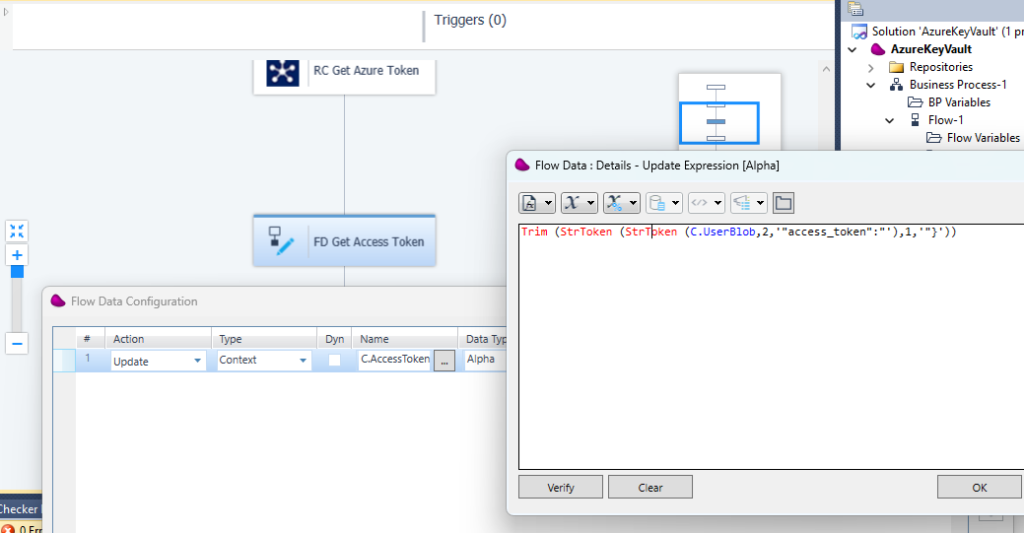
5/ Drag and Drop a Flow Data connector.
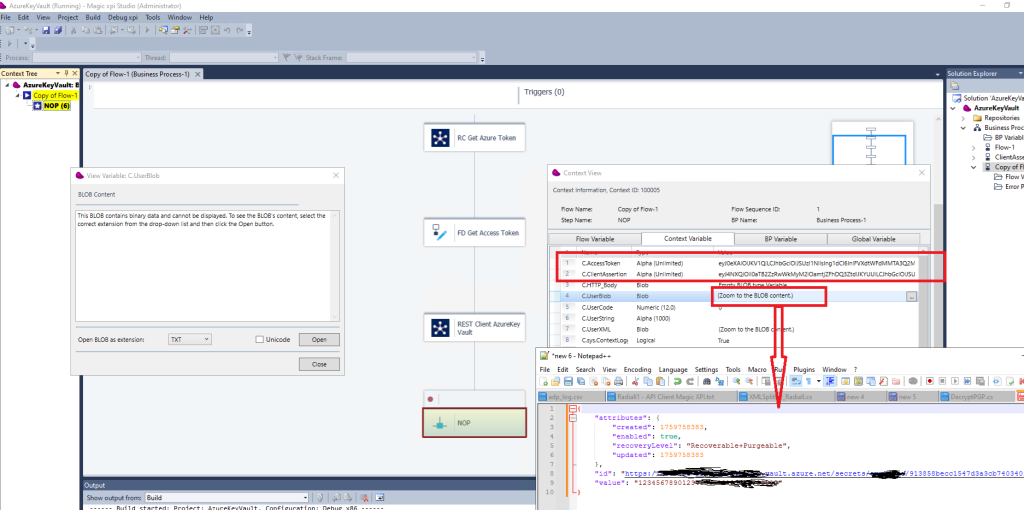
Update C.Accesstoken context variable with Trim (StrToken (StrToken (C.UserBlob,2,' »access_token »: »‘),1,' »}’))
6/ Drag and drop a REST Client connector and link it to AzureKeyVault resource
Set the Bearer token by clicking the Parameters and press OK
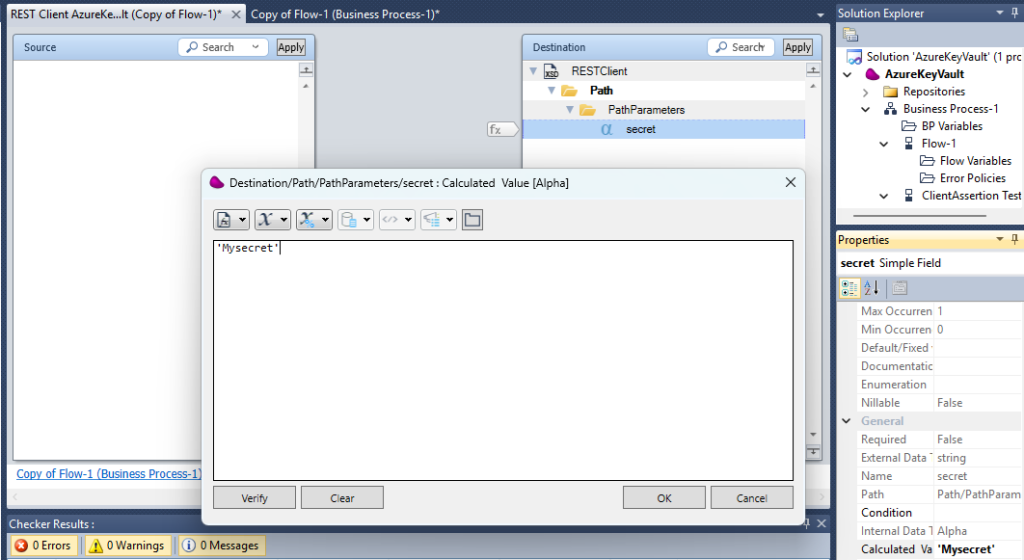
Set the secret name you want to retrieve from your Azure Key Vault
7/ When you execute the flow, you should get the AccessToken,, the ClientAssertion and the content of your secret in C.UserBlob